Table of Contents
- Evolution of Enterprise Security
- Limitations of Traditional Firewalls
- Rise of Cloud-Delivered Firewalls
- Key Benefits of Cloud-Delivered Firewalls
- Implementing Cloud-Delivered Firewalls
- Real-World Applications
- Future of Enterprise Security
- Conclusion
In the face of relentless digital transformation, enterprises must address mounting security risks with agile, innovative tools. The days of relying solely on robust on-premises firewalls are gone; organizations are now adopting new solutions to defend against increasingly advanced cyber threats. Modern businesses require the versatility of solutions such as next generation firewall platforms, which combine deep threat intelligence, centralized management, and scalable cloud architecture for the ultimate in protection. The evolving nature of the enterprise perimeter, driven by distributed workforces, SaaS applications, and IoT integration, necessitates a shift from static defense models to more resilient methods for safeguarding digital assets. Cloud-delivered firewalls are crucial for this new generation of enterprise security, as traditional hardware-based solutions often fail to meet complex security requirements. As attackers become more sophisticated, enterprises must demand continuous updates, dynamic policy enforcement, and granular visibility across all network layers. The global urgency to adopt advanced security solutions is pressing.
Evolution of Enterprise Security
Enterprise security has transformed profoundly in the past two decades. Organizations previously relied on perimeter defense, primarily via physical devices stationed at network boundaries—a strategy effective in centralized office environments with limited entry points. However, business growth, the adoption of cloud computing, and widespread remote work dissolved traditional perimeters. Security must now travel with the user, application, or workload, demanding a more distributed and adaptive approach.
Limitations of Traditional Firewalls
Legacy firewalls were ideal for an era of static boundaries and straightforward network flows, but the modern attack landscape exposes their restrictions:
- Scalability Challenges: Hardware-dependent systems can bottleneck network expansion and require costly physical upgrades when traffic surges.
- Inflexible Response: Legacy appliances make it cumbersome to adapt configuration to new workloads, cloud platforms, or hybrid deployments.
- Operational Overhead: Managing, patching, and updating disparate devices across locations is resource-intensive and prone to errors.
These challenges create security blind spots that sophisticated attackers quickly exploit, underscoring the need for solutions inherently built for fluid enterprise boundaries and workloads.
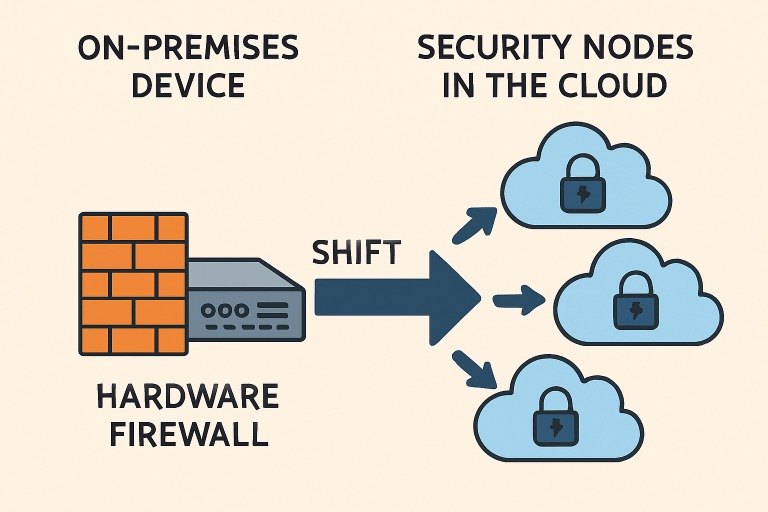
Rise of Cloud-Delivered Firewalls
Cloud-delivered firewalls respond to these challenges by decoupling network security functions from physical devices and placing them directly in the cloud. This shift allows for universal policy enforcement and visibility—regardless of where users connect or where apps are hosted. With centralized management consoles and integration with major cloud providers, these firewalls enable agile, policy-based control while leveraging real-time threat intelligence from globally distributed data centers.
Key Benefits of Cloud-Delivered Firewalls
- Enhanced Scalability: Security resources expand or contract dynamically, accommodating spikes in remote access or application usage without hardware upgrades.
- Operational Flexibility: Organizations can adapt policies instantly as assets move between on-premises, public cloud, or hybrid environments.
- Unified Management: Administrators oversee a single, global security policy from a cloud dashboard, streamlining compliance, troubleshooting, and user provisioning.
- Lower Total Cost of Ownership: Hardware capital expenditures are largely eliminated, replaced by predictable operational expenses tied to real service consumption.
Implementing Cloud-Delivered Firewalls
- Define Objectives: Start by auditing all cloud platforms, business-critical data flows, and security priorities. Clear risk assessments guide architecture choices.
- Vendor Selection: Evaluate providers based on their track record, interoperability, global coverage, service-level agreements, and innovation in threat hunting and intelligence.
- Intelligent Integration: Seamless connection to identity, endpoint, and cloud orchestration systems ensures tight policy enforcement and fast response to threats.
- Continuous Optimization: Automate updates, vulnerability scans, and analytics to keep pace with new threats and optimize security posture over time.
Real-World Applications
Financial services, healthcare, and critical infrastructure enterprises increasingly use cloud-delivered firewalls for compliance, data protection, and zero-trust adoption. For example, VMware Cloud Foundation’s latest advancements help regulated organizations close security gaps presented by evolving AI workloads and complex compliance demands. Read more about VMware’s advancements in cloud security.
Future of Enterprise Security
Cloud-delivered firewalls are positioned at the center of intelligent enterprise defense and are expected to evolve through integration with AI for rapid threat detection and autonomous response. Emerging zero trust frameworks—where no entity is trusted by default—are being extended across hybrid architectures. Palo Alto Networks’ Strata Cloud Manager exemplifies the industry’s shift toward real-time, AI-powered management and next-gen zero trust enablement. Leading technology outlets, such as TechCrunch, continue to report on the convergence of AI, cloud infrastructure, and cybersecurity and how it’s driving innovation and reshaping best practices for modern enterprises. Staying informed on these trends is critical as the boundaries of digital business continue to shift.
Conclusion
Securing today’s interconnected enterprises requires a forward-thinking approach—moving beyond the physical firewall into the cloud. Cloud-delivered firewalls offer unparalleled scalability, flexibility, and intelligence to meet today’s and tomorrow’s cyber threats. By embracing these advances, organizations ensure robust protection, optimize IT operations, and future-proof security posture in an ever-evolving threat landscape.